It was a short week this week, missing Monday in the US. If you are new here, every week I publish a post containing the progress and learning that I did in the past week. The short week made it more difficult to fit in webinars and podcast, but I have a fun webinar set up for next week!
Articles
- Hackers Win $105,000 for Reporting Critical Security Flaws in Sonos One Speakers – Multiple security flaws uncovered in Sonos One wireless speakers could be potentially exploited to achieve information disclosure and remote code execution, the Zero Day Initiative (ZDI) said in a report published last week.
- Pentagon Leaks Emphasize the Need for a Trusted Workforce – Tightening access controls and security clearance alone won’t prevent insider threat risks motivated by lack of trust or loyalty.
- Toyota finds more misconfigured servers leaking customer info – Toyota Motor Corporation has discovered two additional misconfigured cloud services that leaked car owners’ personal information for over seven years.
- SAS Airlines hit by $3 million ransom demand following DDoS attacks – Scandinavian Airlines (SAS) has received a US $3 million ransom demand following a prolonged campaign of distributed denial-of-service (DDoS) attacks against its online services.
- Alert: Hackers Exploit Barracuda Email Security Gateway 0-Day Flaw for 7 Months – Enterprise security firm Barracuda on Tuesday disclosed that a recently patched zero-day flaw in its Email Security Gateway (ESG) appliances had been abused by threat actors since October 2022 to backdoor the devices.
- WordPress force installs critical Jetpack patch on 5 million sites – WordPress.com owner Automat has started force installing a security patch on millions of websites today with the help of the WordPress Security Team to address a critical vulnerability in the Jetpack plug-in.
- Harvard Pilgrim Health Care ransomware attack hits 2.5 million people – Harvard Pilgrim Health Care (HPHC) has disclosed that a ransomware attack it suffered in April 2023 impacted 2,550,922 people, with the threat actors also stealing their sensitive data from compromised systems.
- Russia says US hacked thousands of iPhones in iOS zero-click attacks – Russian cybersecurity firm Kaspersky says some iPhones on its network were hacked using an iOS vulnerability that installed malware via iMessage zero-click exploits.
- Streamers Ditch Netflix for Dark Web After Password Sharing Ban – Disgruntled users are pursuing offers for “full Netflix access” at steeply discounted rates.
- Burton Snowboards discloses data breach after February attack – Leading snowboard maker Burton Snowboards confirmed notified customers of a data breach after some of their sensitive information was “potentially” accessed or stolen during what the company described in February as a “cyber incident.”
Projects
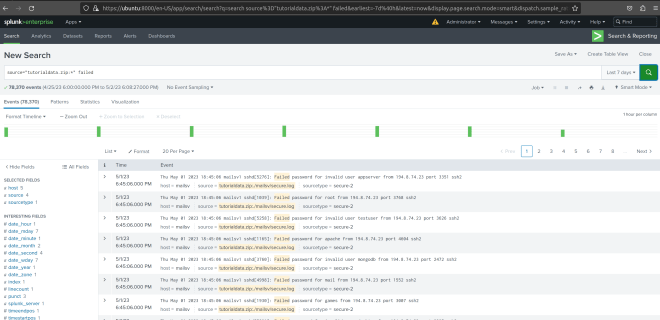
TryHackMe – SOC Level 1 – Network Miner – Completed.